Transport Layer Security (TLS) is a cryptographic protocol designed to provide secure communication over a computer network. It is widely used for securing communications between web browsers and servers, ensuring that data exchanged remains private and integral.
Table of Contents
What is TLS?

- Encryption: TLS encrypts data to ensure that any intercepted data cannot be read by unauthorized parties.
- Integrity: TLS uses message integrity checks to ensure that the data has not been tampered with during transmission.
- Authentication: TLS verifies the identities of the communicating parties, ensuring that data is being sent to and received from the correct servers and clients.
How TLS Works
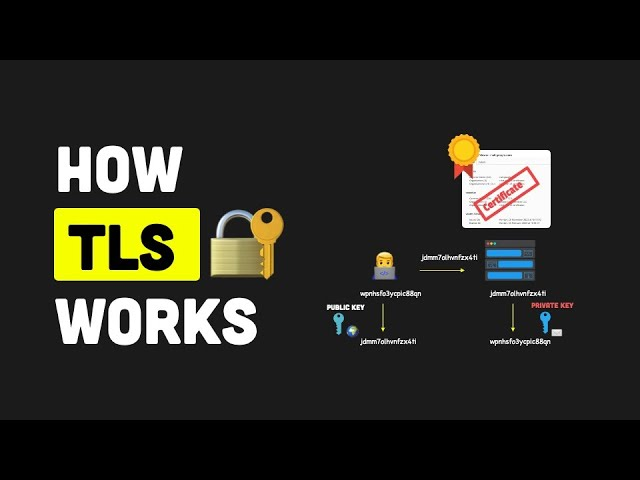
1. Handshake Process
The TLS handshake is the process that initiates a TLS session and negotiates the security parameters. This process includes:
- Client Hello: The client sends a “Client Hello” message to the server, which includes information such as the TLS version it supports, the cipher suites (encryption algorithms) it supports, and a randomly generated number.
- Server Hello: The server responds with a “Server Hello” message, which includes the chosen TLS version, the selected cipher suite, and a randomly generated number.
- Server Certificate: The server sends its digital certificate to the client. This certificate contains the server’s public key and is issued by a trusted Certificate Authority (CA). The client uses this certificate to authenticate the server.
- Key Exchange: The client and server use the public key to securely exchange a pre-master secret. This secret is then used to generate session keys.
- Client Finished: The client sends a “Finished” message encrypted with the session key to indicate that the client part of the handshake is complete.
- Server Finished: The server sends a “Finished” message encrypted with the session key to indicate that the server part of the handshake is complete.
At this point, the handshake is complete, and a secure connection is established.
2. Data Encryption and Integrity
Once the handshake is complete, TLS uses symmetric encryption to secure the data transmitted between the client and server. The session keys generated during the handshake process are used for this encryption.
- Encryption: Data is encrypted using a symmetric encryption algorithm (e.g., AES, ChaCha20), ensuring that it cannot be read by unauthorized parties.
- Integrity: TLS uses message authentication codes (MACs) to verify the integrity of the data. This ensures that the data has not been tampered with during transmission.
3. Session Termination
When the communication between the client and server is complete, the TLS session is terminated. This is done through a process called “session closure,” where both the client and server send a “Close Notify” message to each other. This ensures that both parties agree to terminate the secure session.
Key Components of TLS

- Certificates: Digital certificates issued by trusted CAs verify the identity of the server (and sometimes the client).
- Cipher Suites: A set of algorithms that specify how encryption, key exchange, and integrity checks are performed.
- Public Key Infrastructure (PKI): A framework that manages digital certificates and public-key encryption.
Advantages of TLS

- Security: TLS provides strong encryption, making it difficult for attackers to intercept and read data.
- Trust: Digital certificates verify the identities of the parties involved, building trust in the communication.
- Data Integrity: TLS ensures that data has not been tampered with during transmission.
Conclusion
TLS is an essential protocol for securing communications over the internet. By providing encryption, authentication, and data integrity, it ensures that data remains private and secure between clients and servers.